Test the applications through the public endpoint
Now that you’ve deployed each of the sample workload’s component applications, you’ll test them to determine whether they’re working correctly. If you run into problems, inspect the Container Apps environment logs to figure out what might be missing.
For more information on your Container Apps environment, follow the az containerapp show guidance.
Step-by-step guidance
-
In your web browser, go to the Azure portal.
Go to
Resource groups, and select the resource group you created for this app.Check the resources created for each of the applications.
-
Users will access the app through the api-gateway, which you previously configured to accept external traffic. To test that it’s working correctly, you’ll need to open it in your browser. To find its address, go to the Azure portal and find the application URL for the api-gateway container app. Alternatively you can run the following CLI command to get the URL:
api_gateway_FQDN=$(az containerapp show \ --resource-group $RESOURCE_GROUP \ --name api-gateway \ --query properties.configuration.ingress.fqdn \ -o tsv) echo https://$api_gateway_FQDN -
You created the Spring Boot Admin component in your Azure Container Apps environment. To test this app, go to the portal and locate your Azure Container Apps environment. To find the Admin for Spring service, under
Settings>Services, get the Admin dashboard URL. Alternatively, use the following CLI:sba_FQDN=$(az containerapp env java-component admin-for-spring show \ --environment $ACA_ENVIRONMENT \ --resource-group $RESOURCE_GROUP \ --name $JAVA_SBA_COMP_NAME \ --query properties.ingress.fqdn \ -o tsv) echo https://$sba_FQDN -
In a browser window, connect to the Admin app URL. This shows your applications’ running info.
(Optional) If you failed to open the page with the error `Could not authenticate user with requested resource`, click here for further instructions.
- Go to the portal, and find your Azure Container Apps environment.
- In the left menu, select
Access control (IAM)and then selectAdd>Add role assignment. - In the
Roletab, search and selectContainer Apps ManagedEnvironments Contributor. On the Members tab, select assignee typeUser,group, orservice principal, and then search and select your account using the Select members menu. - Select Review + Assign to finish assigning the role.
Alternatively, you can use the following CLI command to assign the roll:
az role assignment create --assignee $USER_NAME --scope $ACA_ENVIRONMENT_ID --role 'Container Apps ManagedEnvironments Contributor'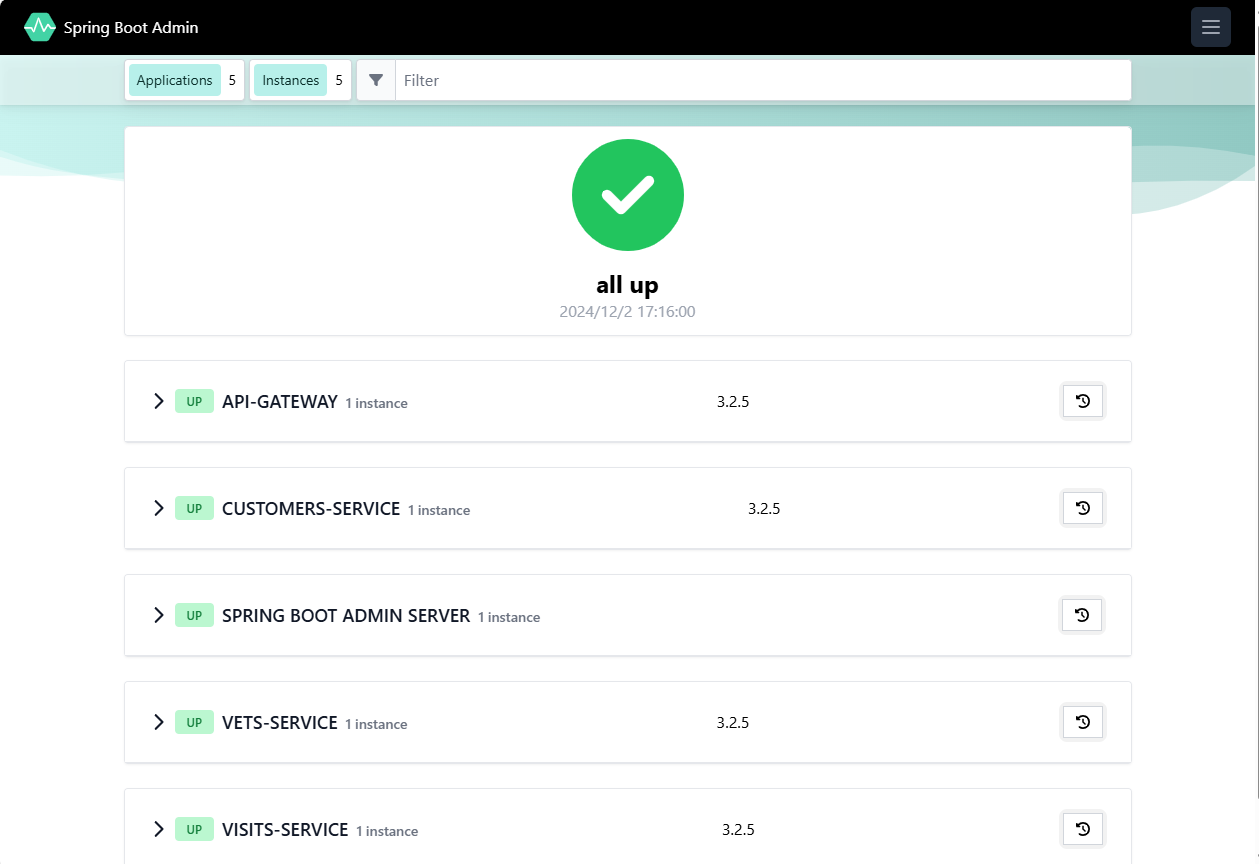
Select Wallboard and then select one of the component applications. The Admin server will then show you internal info for that apps.
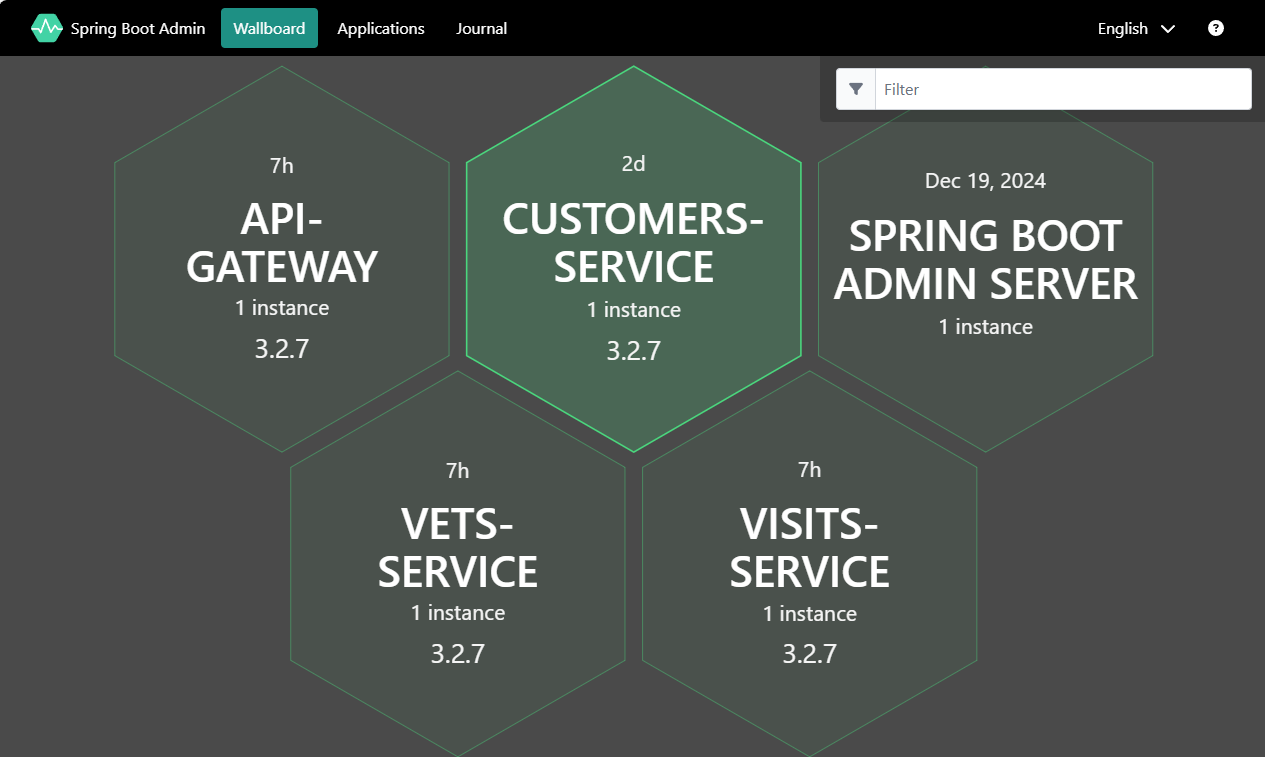
-
Use a browser window to connect to the
api-gateway. This will allow you to test the combined example Spring Petclinic applications.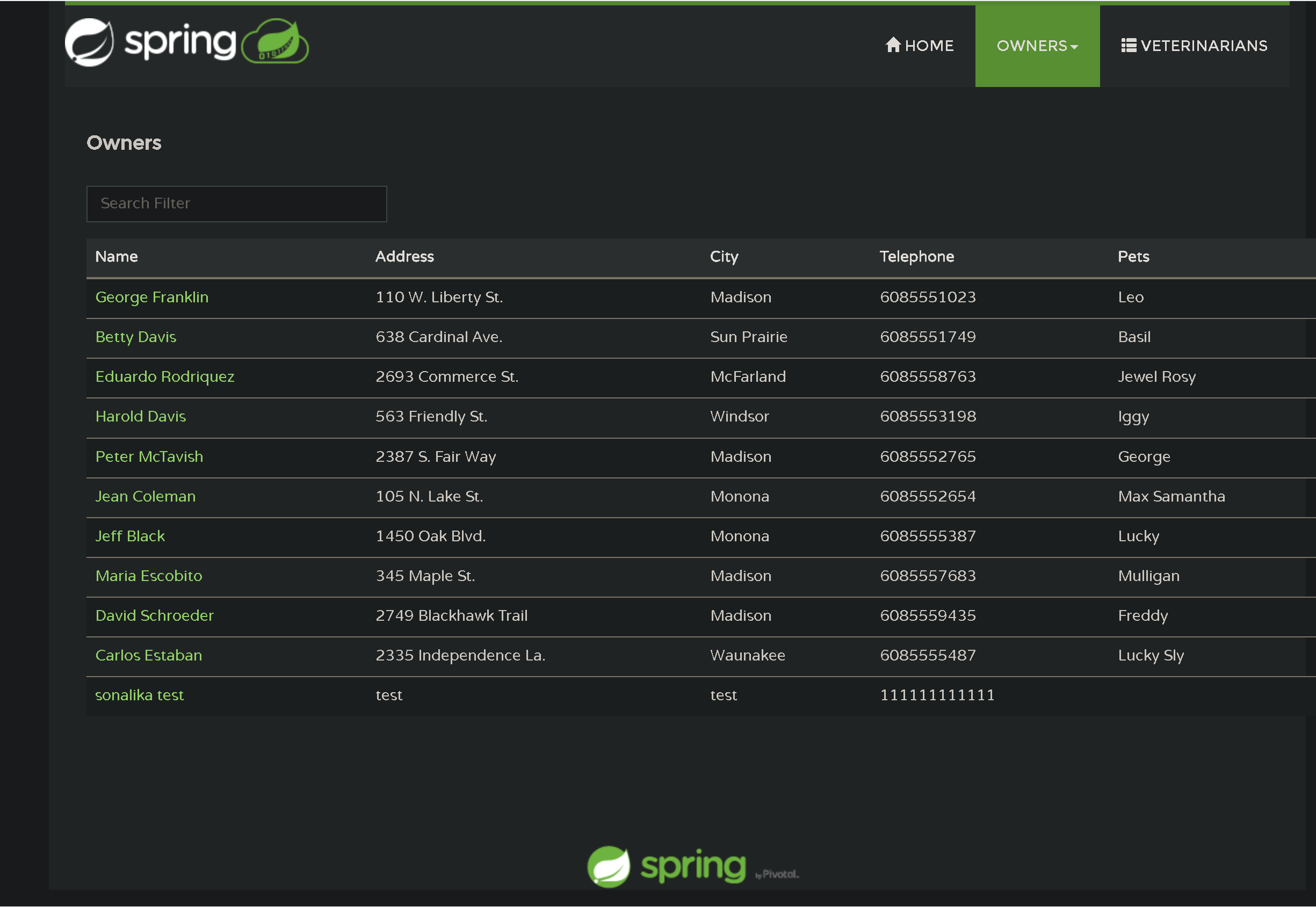
(Optional) If you aren’t finding data in your application, click here for troubleshooting information.
You can troubleshoot this issue by interactively connecting to your Azure Database for MySQL - Flexible Server instance and querying your databases and tables.
az mysql flexible-server connect -n $MYSQL_SERVER_NAME -u $MYSQL_ADMIN_USERNAME --interactiveTo sign in, enter your MYSQL_ADMIN_PASSWORD. Once connected you can use queries like the following to test the database:
show databases; use petclinic; show tables; select * from owners;For the Azure Database for MySQL - Flexible Server connection to work, you’ll need to have your local IP address added to the Azure Database for MySQL - Flexible Server firewall allowed list.